The Office of the Australian Information Commissioner has released its finalised Guide to securing personal information.
The Guide is intended to help agencies and organisations (including credit providers and tax file number recipients) to meet their obligations under the Australian Privacy Principles (particularly APP 11) to take reasonable steps to protect personal information.
The guide is not legally binding. However, the Office of the Australian Information Commissioner (OAIC) will refer to thes guide when undertaking its Privacy Act functions, including when investigating whether an entity has complied with its personal information security obligations
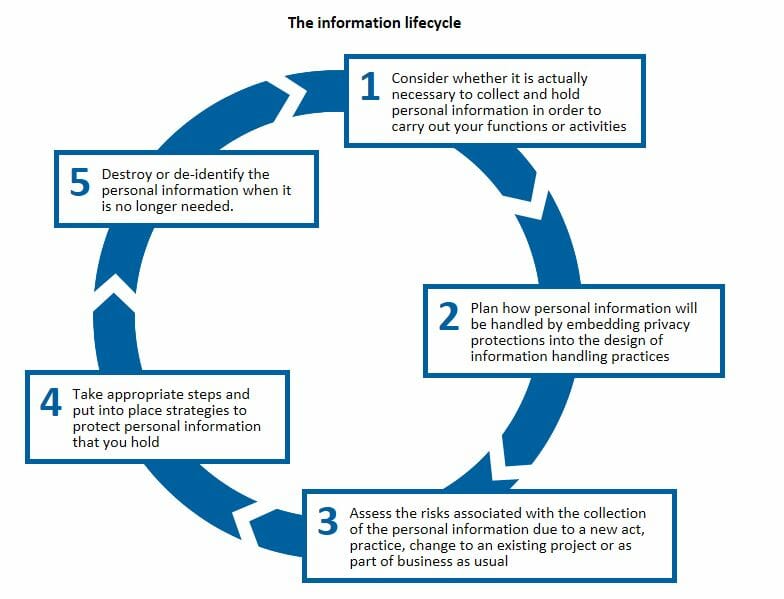
The Guide emphasises the five steps in the information lifecycle (see diagram below, click to enlarge) that are necessary for agencies and organisations to take in assessing whether to collect personal information, how to protect it, and what to do with it once it is no longer needed.

What qualifies as reasonable steps to ensure the security of personal information depends on the circumstances, including the following:
•the nature of your organisation
•the amount and sensitivity of the personal information held
•the possible adverse consequences for an individual in the case of a breach
•the practical implications of implementing the security measure, including the time and cost involved
•whether a security measure is itself privacy invasive.
These circumstances will also influence the reasonable steps you should take to destroy or de-identify personal information.
The guide recommends steps and strategies in the following areas:
•Governance, culture and training.
•Internal practices, procedures and systems.
•ICT security.
•Access security.
•Third party providers (including cloud computing).
•Data breaches.
•Physical security.
•Destruction and de-identification.
•Standards.

